Virus hoax
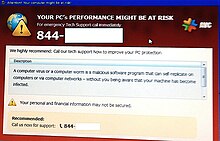
A computer virus hoax is a message warning the recipients of a non-existent computer virus threat. The message is usually a chain e-mail that tells the recipients to forward it to everyone they know, but it can also be in the form of a pop-up window.[1][2]
Identification
[edit]Most hoaxes are sensational in nature and easily identified by the fact that they indicate that the virus will do nearly impossible things, like blow up the recipient's computer and set it on fire, or less sensationally, delete everything on the user's computer. They often include fake announcements claimed to originate from reputable computer organizations together with mainstream news media. These bogus sources are quoted in order to give the hoax more credibility. Typically, the warnings use emotive language, stress the urgent nature of the threat and encourage readers to forward the message to other people as soon as possible.[2]
Virus hoaxes are usually harmless and accomplish nothing more than annoying people who identify it as a hoax and wasting the time of people who forward the message. Nevertheless, a number of hoaxes have warned users that vital system files are viruses and encourage the user to delete the file, possibly damaging the system. Examples of this type include the jdbgmgr.exe virus hoax and the SULFNBK.EXE hoax.[3][4]
Some consider virus hoaxes and other chain e-mails to be a computer worm in and of themselves. They replicate by social engineering—exploiting users' concern, ignorance, and disinclination to investigate before acting.
Hoaxes are distinct from computer pranks, which are harmless programs that perform unwanted and annoying actions on a computer, such as randomly moving the mouse, turning the screen display upside down, etc.
Action
[edit]Anti-virus specialists agree that recipients should delete virus hoaxes when they receive them, instead of forwarding them.[5][6]
McAfee says:
We are advising users who receive the email to delete it and DO NOT pass it on as this is how an email HOAX propagates.[5]
F-Secure recommends:
Do not forward hoax messages.
Hoax warnings are typically scare alerts started by malicious people – and passed on by innocent individuals that think they are helping the community by spreading the warning.
Corporate users can get rid of the hoax problem by simply setting a strict company guideline: End users must not forward virus alarms. Ever. It's not the job of an end user anyway. If such message is received, end users could forward it to the IT department but not to anyone else.[6]
Comparison
[edit]| Name | Alias(es) | Origin | Author | Description |
|---|---|---|---|---|
| Antichrist | (none) | United Kingdom | Dylan Nicholas | A hoax that warned about a supposed virus discovered by Microsoft and McAfee named "Antichrist", telling the user that it is installed via an e-mail with the subject line: "SURPRISE?!!!!!!!!!!" after which it destroys the zeroth sector of the hard disk, rendering it unusable.[7] |
| AF/91 | April Fool's 1991 | United States | John Gantz | A 1991 InfoWorld article detailing a cyberweapon developed by the United States Intelligence Community for use against Iraq during the Gulf War, capable of "eating" a user's windows, that had spread past its intended target and "mutated" to be able to destroy the display of any computer with windowing technology, namely Windows 3.0. Intended as an April Fools' Day joke and never actually existed, but was mistakenly reported as a real cyberweapon (albeit without mentions of the spread and mutation) by several news organizations well into the early 2000s.[8] |
| Black in the White House | Black Muslim in the White House | Unknown | A chain message beginning around 2006. It begins with the message warning of a virus that hides in an attachment labeled "Black in White House" or something similar, saying that if the user opens it, then it opens an Olympic Torch that burns down the C disk.[9] | |
| Budweiser Frogs | BUDSAVER.EXE | Unknown | Unknown | Would supposedly erase the user's hard drive and steal the user's screen name and password.[10] |
| Goodtimes virus | (none) | Unknown | Unknown | Warnings about a computer virus named "Good Times" began being passed around among Internet users in 1994. Was supposedly transmitted via an email bearing the subject header "Good Times" or "Goodtimes," hence the virus's name, and the warning recommended deleting any such email unread. The virus described in the warnings did not exist, but the warnings themselves, were, in effect, virus-like.[11] |
| Invitation attachment | (Allright now/I'm just sayin) | United States | Jim Flanagan | An e-mail spam in 2006 that advised computer users to delete an email, with any type of attachment that stated "invitation" because it was a computer virus. This is also known as the Olympic Torch virus hoax (see below).[12] |
| Jdbgmgr.exe | (bear.a) | Unknown | Unknown | Involved an e-mail spam in 2002 that advised computer users to delete a file named jdbgmgr.exe because it was a computer virus. jdbgmgr.exe, which had a little teddy bear-like icon (The Microsoft Bear), was actually a valid Microsoft Windows file, the Debugger Registrar for Java (also known as Java Debug Manager, hence jdbgmgr).[3] |
| Life is beautiful | Life is wonderful | Brazil (first reported) | Supposedly a hacker with the alias "Life owner" or "Dono da vida" | Spread through the Internet around January 2001. It was a virus attached to an e-mail, which was spread around the Internet. The attached file was supposedly called "Life is beautiful.pps" or "La vita è bella.pps".[13] |
| NVISION DESIGN, INC. games ("Frogapult," "Elfbowl") | Sometimes included their other game "Y2KGame" | Unknown | Unknown | Programs were actual, legitimate computer games; author claimed that they were viruses which would "wipe out" the user's hard drive on Christmas.[14] |
| Olympic Torch | "Postcard" or "Postcard from Hallmark" | Unknown | Unknown | A series of e-mails first sent in February 2006. The "virus" referred to by the e-mail does not actually exist. The hoax e-mail warns recipients of a recent outbreak of "Olympic Torch" viruses, contained in e-mails titled "Invitation", which erase the hard disk of the user's computer when opened. The hoax email further purports the virus to be acknowledged by such reputable sources as CNN, McAfee, and Microsoft as one of the most dangerous viruses yet reported. This email, which was started in February 2006, is safe to delete when the user wants.[12] |
| SULFNBK.EXE Warning | none | Unknown | Unknown | SULFNBK.EXE (short for Setup Utility for Long File Name Backup) is an internal component of the Microsoft Windows operating system (in Windows 98 and Windows Me) for restoring long file names. The component became famous in the early 2000s as the subject of an e-mail hoax. The hoax claimed that SULFNBK.EXE was a virus, and contained instructions to locate and delete the file. While the instructions worked, they were needless and (in some rare cases, for example, when the long file names are damaged and need to be restored) can cause disruptions, as SULFNBK.EXE is not a virus, but instead an operating system component.[4] |
| System32 | None | United States | Unknown | System32 is a critical Windows System Folder, which would render the Computer inoperable if deleted. Due to the nature of how critical this folder is, several hoaxes were made telling unsespecting or novice users that System32 is a virus that Microsoft preintalled on all Windows PCs to slow them down. |
Telephone scam
[edit]A telephone scam, commonly operated from call centres based in India, has been active since 2008. The victim is quoted his or her name and address, and is told: "I'm calling for Microsoft (or an entity that sounds like it is connected to Microsoft, such as the "Windows Service Center" or "Windows Technical Department"). We've had a report from your internet service provider of serious virus problems from your Windows computer." The victim is then directed to open the Windows event viewer, which displays apparently critical warnings, and is directed to a website to download an application to allow the scammer to control his or her computer remotely. The caller supposedly fixes the problems and demands a fee for the service. In addition to the fraudulent fee, the process usually enables malware to be uploaded to the victim's computer.[15]
Parodies
[edit]The virus hoax has become part of the culture of the twenty-first century and the gullibility of novice computer users convinced to delete files on the basis of hoaxes has been parodied in several popular jokes and songs.
One such parody is "Weird Al" Yankovic's song "Virus Alert" from the album Straight Outta Lynwood. The song makes fun of the exaggerated claims that are made in virus hoaxes, such as legally changing your name or opening a rift in time and space.[16]
Another parody of virus hoaxes is the honor system virus which has been circulated under the name Amish Computer Virus, manual virus, the Blond Computer Virus, the Irish Computer Virus, the Syrian Computer Virus, the Norwegian Computer Virus, Albanian Virus, Newfie Virus, the Unix Computer Virus, the Mac OS 9 virus, Discount virus and many others. This joke email claims to be authored by the Amish or other similar low-technology populations who have no computers, programming skills or electricity to create viruses and thus ask users to delete their own hard drive contents manually after forwarding the message to their friends.[17][dead link]
The Tuxissa virus is another parody of the virus hoax, based on the concept of the Melissa virus, but with its aim of installing Linux on the victim's computer without the owner's permission. The story says that it was spread via e-mail, contained in a message titled "Important Message About Windows Security". It was supposed to first spread the virus to other computers, then download a stripped-down version of Slackware and uncompress it onto the hard disk. The Windows Registry is finally deleted and the boot options changed. The virus then reboots the computer, leaving the user facing the Linux login prompt with all their Windows security problems solved.[18]
See also
[edit]References
[edit]- ^ "Virus hoax". Malwarebytes Labs. Retrieved 1 December 2020.
- ^ a b "What is a hoax? - Panda Security". www.pandasecurity.com. Retrieved 1 December 2020.
- ^ a b Mikkelson, Barbara and David P. (January 2008). "JDBGMGR.EXE Virus". Retrieved 8 August 2011.
- ^ a b Mikkelson, Barbara and David P. (January 2008). "SULFNBK.EXE Virus". Retrieved 8 August 2011.
- ^ a b McAfee, Inc (December 2003). "Virus Profile: A Virtual Card For You Hoax". Retrieved 30 November 2018.
- ^ a b F-Secure Corporation (2009). "Hoax Warnings". Archived from the original on 22 June 2012. Retrieved 14 June 2012.
- ^ Gutierrez, Ralph (July 2001). "Antichrist Hoax". Archived from the original on 1 January 2007. Retrieved 8 August 2011.
- ^ Smith, George (10 March 2003). "Iraqi Cyberwar: an Ageless Joke". SecurityFocus. Archived from the original on 5 June 2003. Retrieved 13 November 2015.
- ^ "Black Muslim in the White House". snopes.com. 20 June 2013. Retrieved 17 January 2014.
- ^ Mikkelson, Barbara and David P. (January 2008). "Budweiser Frogs Virus". Retrieved 8 August 2011.
- ^ Jones, Les (December 1998). "Good Times Virus Hoax Frequently Asked Questions". Retrieved 8 August 2011.
- ^ a b Christensen, Brett M. (2008). "Olympic Torch Invitation Virus Hoax". Retrieved 8 August 2011.
- ^ Koris, George (15 January 2002). "Life is beautiful Hoax". Symantec.com. Symantec. Archived from the original on 7 March 2007. Retrieved 8 August 2011.
- ^ Symantec Corporation (February 2007). "FROGAPULT, ELFBOWL, Y2KGAME Virus Hoax". Archived from the original on 27 May 2009. Retrieved 8 August 2011.
- ^ Charles Arthur (18 July 2010). "Virus phone scam being run from call centres in India". Guardian News and Media Limited. Retrieved 1 May 2012.
- ^ "Weird Al unleashes his new album with a Bill Plympton Video DON'T DOWNLOAD THIS SONG!!!". Ain't It Cool News. 11 September 2006. Retrieved 8 August 2011.
- ^ Pearson, Karl (May 2000). "Humor: For a good time..." Retrieved 8 August 2011.
- ^ Baughn, James (March 1999). "Attack of the Tuxissa Virus". Archived from the original on 11 August 2004. Retrieved 17 April 2009.
External links
[edit]
